Journalling
So I don’t pass the PJOR certification. I do not need to wait for results since I only submitted thirty points worth of the exam. I am going to hold off re taking it and focus down the road of the other certifications I want to take that are more technical. After a bit more research into order of which to take certifications I might change some things up. Regardless though the PJPT and PJWT are the first up in the wave of certifications to get done.
Decided to start with thePJPT certification based on recommendations from other people. Since the certification is also a bulk of the PNPT course I am wondering If I want to switch the learning path or keep hop scotching between Pen Testing and web app security.
Daily learning recap
- Being a Penetration Tester has three major aspects to the job
- Assessments
- What everyone thinks of when it comes to pentesting. This is where you are doing the hacking.
- Report Writing
- Sharing the discoveries of you findings and how to remedy them in written form.
- Debriefing
- Sharing your report in a meeting aspect.
- Assessments
- The first report you write is a draft
- I found this part interesting. I assume a customer can come back stating something is not accurate or critical. Maybe getting security certified these reports have to be shared and can shine the company in a bad light? I want to know more about this
- There are a bunch of different types of assessments
- External - Where you are trying to get into the organizations network from the inside
- Internal - Where you are trying to see what you can do once you are inside the organizations network
- Web Application - Where you are assessing an organizations web application
- Wireless Network - Seeing if you can hack into an organizations internet
- Physical - physically be able to get into an organizations restricted areas.
- Report writing Typically needs to be delivered within a week of the pentest
- Has to be high level and technical
What I need to learn more oftodo
- OSI Model - Possibly make flash cards of this since I have learned it a few times and do not remember it. Possibly find a more in depth video on the OSI model or networking.
- Possibly just learn more IT stuff including IP Address stuff
Raw Notes
- What is the difference between internal and external penetration tests?
- Internal: This is assessing the organizations security from inside the network.
- Relies heavily on Active Directory
- last 32-40 hours with an additional 8-16 report writing
- External: an external pentest are more straight forward and are essentially trying to do the pentest from outside the org and its network. UseOSINT to gather information. These are the most common engagement because a lot of security compliance require an external pentest yearly.
- Typically lasts 32-40 hours with another 8-6 for report writing.
- Internal: This is assessing the organizations security from inside the network.
- Web Application Pentest
- Second most common pentest
- Asses the organizations web application security
- Focuses heavily on web-baed attacks and the OWASP testing guidelines
- Typically lasts 32-40 hours with another 8-16 hours for report writing.
- Wireless Network Pentest
- Assessing an organizations wireless network security
- methodology changes based on guest vs WPA2-PSK vs WPA2 Enterprise
- Need a wireless adapter
- Typically lasts 4-8 hours per SSID and another 2 -4 hours of report writing
- Physical Pentest & Social engineering
- Assesing an organizations physical security
- Methodology depends on task and goals
- Typically lasts 16-40 hours with another 4-8 for report writing
- can last 16-40 hours or 4-8 hours
- other assessments
- Mobile pentesting
- IoT Pentesting
- Red Team Engagements
- Stealth and long lasting
- Purple Team Engagements
- blue and red team working together to harden security
- Report Writing
- typically delivered within a week after the engagement
- High level summary for non technical folks
- Technical recommendations that also include remediation should be clear to both execs and technical folks
- typically delivered within a week after the engagement
- Debrief
- Walk through your report doing non technical and technical for both types of people on the call
- The debrief gives the customer the ability to ask questions and address any concerns before a final report is released.
- The original report is a draft.
- Why not to get into this career?
- For the money
- It is good pay but is work
- Some one who does not like to study
- Do not like being complacent
- You are not passionate about the field
- For the money
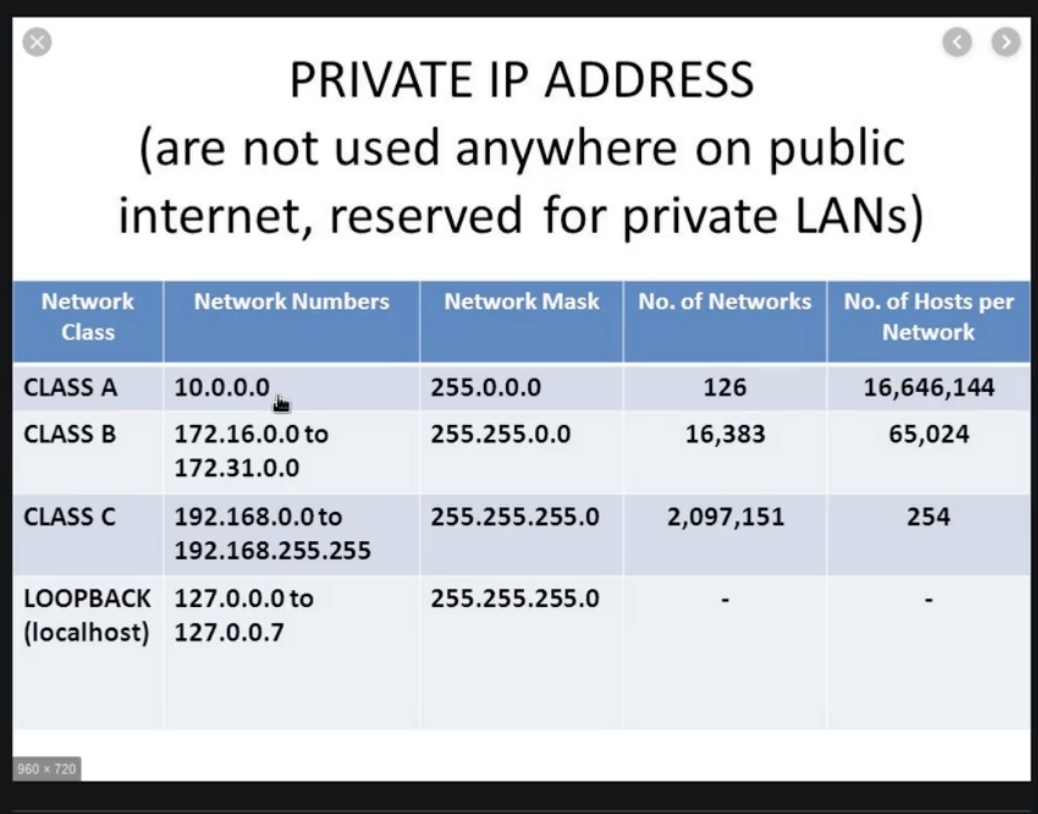
- IP Addresses
- communicate over layer 3
- Learn the OSI Modeltodo
- NAT - Network address translation
- Private IP addresses are in 4 claSSES
- Might want to look into learning the gist of networking better.